Introduction
Last time, I posted a solution that shows how I approached the fourth lab of MemLabs challenges. This post continues to show how I got the flags for the fourth lab of MemLabs, called “Black Tuesday”.
Extracting the clues from description
The following is the challenge description that contains the needed clues to solve this lab.
We received this memory dump from our client recently. Someone accessed his system when he was not there and he found some rather strange files being accessed. Find those files and they might be useful. I quote his exact statement :
“The names were not readable. They were composed of alphabets and numbers but I wasn’t able to make out what exactly it was.”
Also, he noticed his most loved application that he always used crashed every time he ran it. Was it a virus?
Note-1: This challenge is composed of 3 flags. If you think 2nd flag is the end, it isn’t!! :P
Note-2: There was a small mistake when making this challenge. If you find any string which has the string “L4B_3_D0n3!!” in it, please change it to “L4B_5_D0n3!!” and then proceed.
Note-3: You’ll get the stage 2 flag only when you have the stage 1 flag.
I managed to extract the following two clues:
- The file names were not readable. They were composed of alphabets and numbers, is a hint to look for files with names containing alphabets and numbers.
- He noticed his most loved application that he always used crashed every time he ran it. Was it a virus?, is a hint to inspect the crashing application.
Finding the image profile
First of all, we need to find the profile of the memory image using imageinfo plugin as in the following command.
CommandLine
$ ./vol -f MemoryDump_Lab5.raw imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/oviche/Desktop/memlabs/MemoryDump_Lab5.raw)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf800028460a0L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80002847d00L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2019-12-20 03:47:57 UTC+0000
Image local date and time : 2019-12-20 09:17:57 +0530The first suggested profile “Win7SP1x64” worked in my case.
Finding the crashed application
Firstly, I tried to look for the running processes using the pslist plugin to find any clues.
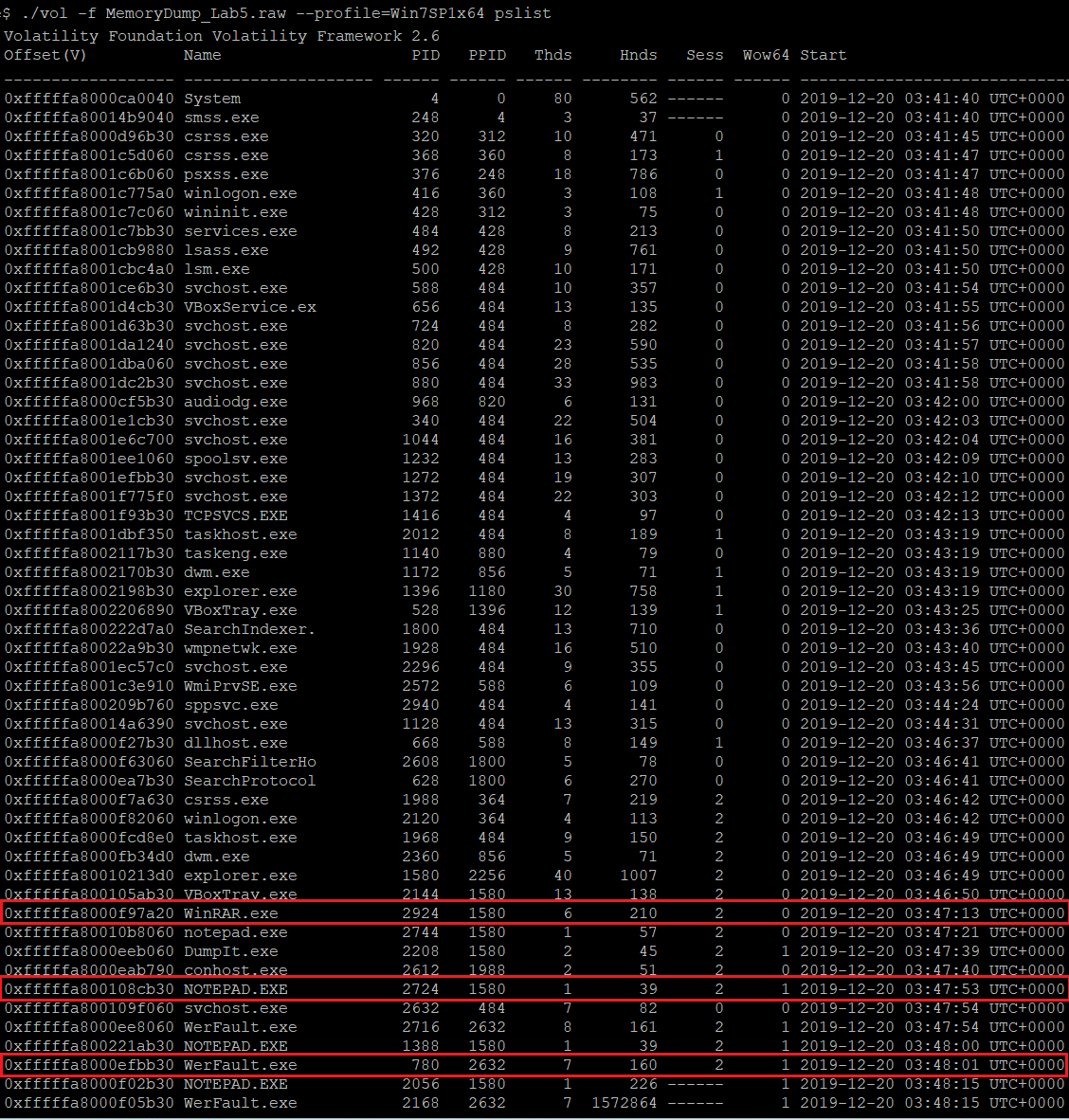 (The running processes)
(The running processes)
Three interesting processes are highlighted above. Let’s use the cmdline plugin to find the command line arguments for these processes.
CommandLine
$ ./vol -f MemoryDump_Lab5.raw cmdline | grep -e "WerFault\|NOTEPAD\|WinRAR" -C 1
Volatility Foundation Volatility Framework 2.6
************************************************************************
WinRAR.exe pid: 2924
Command line : "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\SmartNet\Documents\SW1wb3J0YW50.rar"
************************************************************************
--
************************************************************************
NOTEPAD.EXE pid: 2724
Command line : "C:\Users\SmartNet\Videos\NOTEPAD.EXE"
************************************************************************
--
************************************************************************
WerFault.exe pid: 2716
Command line : C:\Windows\SysWOW64\WerFault.exe -u -p 2724 -s 156
************************************************************************
NOTEPAD.EXE pid: 1388
************************************************************************
WerFault.exe pid: 780
Command line : C:\Windows\SysWOW64\WerFault.exe -u -p 1388 -s 156
************************************************************************
NOTEPAD.EXE pid: 2056
************************************************************************
WerFault.exe pid: 2168The above output of the previous command contains the following important three pieces of information:
- The command line arguments for WinRAR.exe contain SW1wb3J0YW50.rar, which has an alphanumeric name.
- WerFault process that gets executed when any process crashes. Its command line specifies the PID of the crashed process.
- NOTEPAD.EXE exists and is executed from a different path than the normal one.
First, let us focus our attention on WerFault that contains PID(s) (specified by switch “-p”) of the crashed processes within its command line argument.
Thus, Based on the previous command’s output, the processes with PID equals 1388 and 2724 are the ones that crashed, and both point to NOTEPAD.EXE based on the pslist output.
Now, I will dump the process with one of the PID(s) for the crashed processes using procdump.
CommandLine
$ ./vol -f MemoryDump_Lab5.raw --profile=Win7SP1x64 procdump -p 2724 -D DumpedFiles5
Volatility Foundation Volatility Framework 2.6
Process(V) ImageBase Name Result
------------------ ------------------ -------------------- ------
0xfffffa800108cb30 0x0000000001000000 NOTEPAD.EXE OK: executable.2724.exeThen, I inspected the process using a Cutter disassembler. While crawling through the entry point function, I found the characters for the third flag.
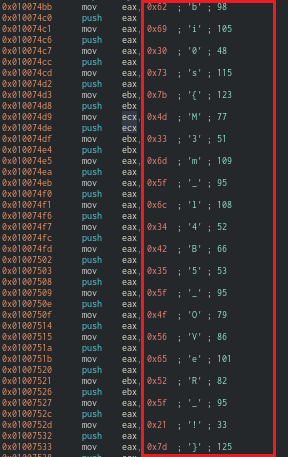 (The disassembly of NOTEPAD.EXE)
(The disassembly of NOTEPAD.EXE)
The third flag is bi0s{M3m_l4B5_OVeR_!}
Inspecting the SW1wb3J0YW50.rar
Now, let’s try to dump SW1wb3J0YW50.rar using the plugins filescan and dumpfiles.
CommandLine
$ ./vol -f MemoryDump_Lab5.raw --profile=Win7SP1x64 filescan | grep "SW1wb3J0YW50.rar"
Volatility Foundation Volatility Framework 2.6
0x000000003eed56f0 1 0 R--r-- \Device\HarddiskVolume2\Users\SmartNet\Documents\SW1wb3J0YW50.rar
$ ./vol -f MemoryDump_Lab5.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003eed56f0 -D DumpedFiles5
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x3eed56f0 None \Device\HarddiskVolume2\Users\SmartNet\Documents\SW1wb3J0YW50.rarThen, I tried to extract the file. However, I found that it needs a password, which probably is the flag of the first stage.
CommandLine
$ unrar x SW1wb3J0YW50.rar
UNRAR 6.11 beta 1 freeware Copyright (c) 1993-2022 Alexander Roshal
Extracting from SW1wb3J0YW50.rar
Enter password (will not be echoed) for Stage2.png:I have no clue how I can get this password. So I tried different plugins like clipboard but no luck. After some time, I found that the plugin iehistory showed a base64 encoded filename as appear below.
iehistory: helps to find entries of the index.dat file, which is a database of recent IE browser activities. However, it also contains browser activities for processes that use IE through COM object or Wininet APIs (such as InternetOpenUrl, InternetReadFile, HttpSendRequest, etc..).
CommandLine
$ ./vol -f MemoryDump_Lab5.raw --profile=Win7SP1x64 iehistory
Volatility Foundation Volatility Framework 2.6
**************************************************
Process: 1396 explorer.exe
Cache type "DEST" at 0x635910f
Last modified: 2019-12-20 09:16:37 UTC+0000
Last accessed: 2019-12-20 03:46:38 UTC+0000
URL: Alissa Simpson@file:///C:/Windows/AppPatch/ZmxhZ3shIV93M0xMX2QwbjNfU3Q0ZzMtMV8wZl9MNEJfNV9EMG4zXyEhfQ.bmpAfter decoding the base64 encoded filename, the stage-1 flag is printed.
CommandLine
$ echo "ZmxhZ3shIV93M0xMX2QwbjNfU3Q0ZzMtMV8wZl9MNEJfNV9EMG4zXyEhfQ" | base64 -d
flag{!!_w3LL_d0n3_St4g3-1_0f_L4B_5_D0n3_!!}Finally, I used this stage-1 flag to successfully decompress SW1wb3J0YW50.rar.
CommandLine
$ unrar x SW1wb3J0YW50.rar
Extracting from SW1wb3J0YW50.rar
Enter password (will not be echoed) for Stage2.png:
Would you like to replace the existing file Stage2.png
83274 bytes, modified on 2019-12-19 07:24
with a new one
83274 bytes, modified on 2019-12-19 07:24The following stage-2.png containing the stage-2 flag, was inside SW1wb3J0YW50.rar.
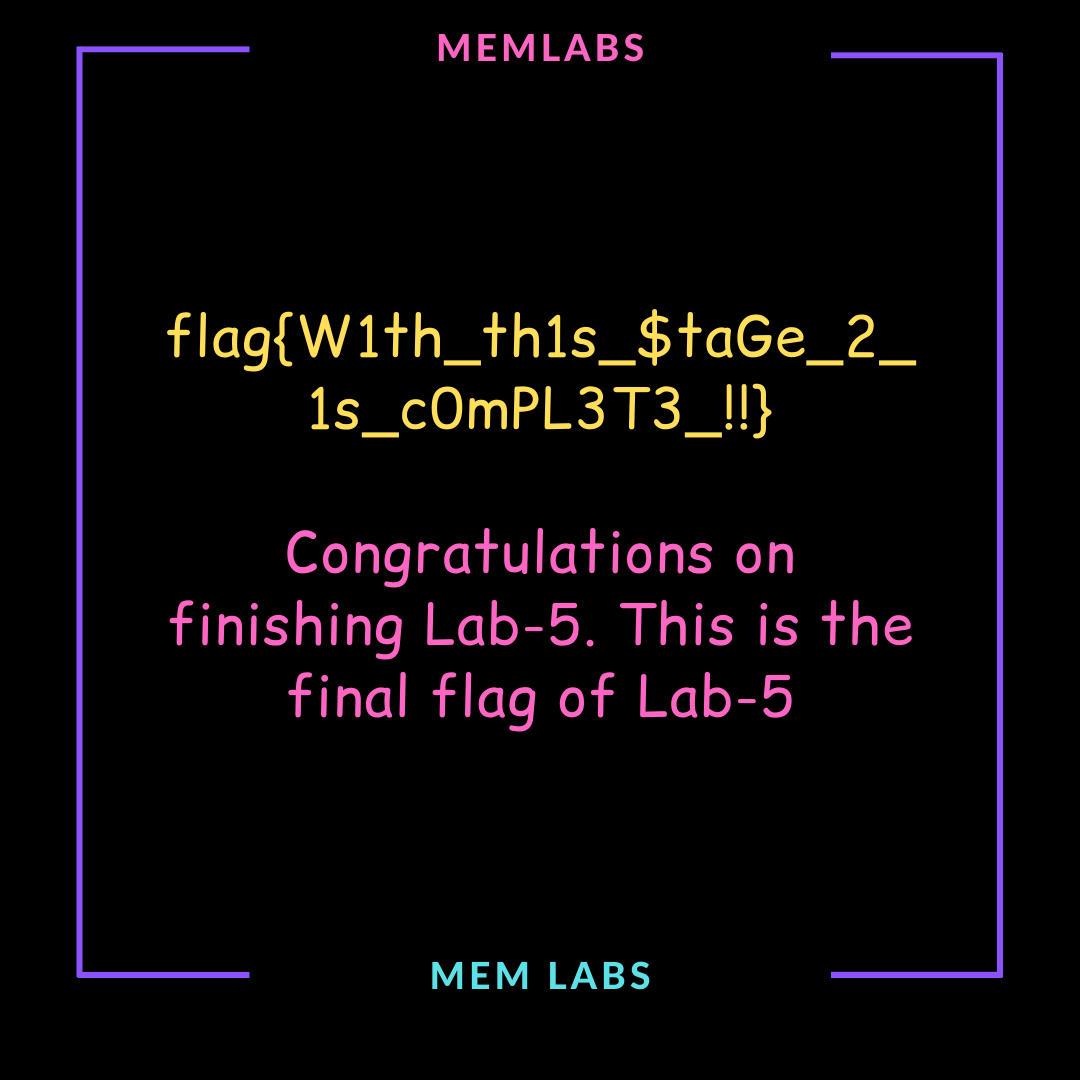 (Stage-2 flag)
(Stage-2 flag)
Conclusion
The final solution is the concatenation of three flags:
flag{!!_w3LL_d0n3_St4g3-1_0f_L4B_5_D0n3_!!} flag{W1th_th1s_$taGe_2_1s_cOmPL3T3_!!} bi0s{M3m_l4B5_OVeR_!}