Introduction
Last time, I posted a solution that shows how I approached the third lab of MemLabs challenges. This post continues to show how I got the flags for the fourth lab of MemLabs, called “The Evil’s Den”.
Extracting the clues from description
The following is the challenge description that contains the needed clues to solve this lab.
My system was recently compromised. The Hacker stole a lot of information but he also deleted a very important file of mine. I have no idea on how to recover it. The only evidence we have, at this point of time is this memory dump. Please help me.
The only clue that exist is that we need to search for the deleted important file.
Finding the image profile
First of all, we need to find the profile of the memory image using imageinfo plugin as in the following command.
CommandLine
$ ./vol -f MemoryDump_Lab4.raw imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/oviche/Desktop/memlabs/MemoryDump_Lab4.raw)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf800027f60a0L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff800027f7d00L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2019-06-29 07:30:00 UTC+0000
Image local date and time : 2019-06-29 13:00:00 +0530The first suggested profile “Win7SP1x64” worked in my case.
Locating the important file
At first, I looked for the running processes using pslist so it may give an idea of how to find that file, but no luck.
So I thought to look for file that contain “important” in its name using the following command.
CommandLine
$ ./vol -f MemoryDump_Lab4.raw --profile=Win7SP1x64 filescan | grep -i "important"
Volatility Foundation Volatility Framework 2.6
0x000000003f939720 2 0 RW-rw- \Device\HarddiskVolume2\Users\SlimShady\AppData\Roaming\Microsoft\Windows\Recent\Important.lnk
0x000000003fc398d0 16 0 R--rw- \Device\HarddiskVolume2\Users\SlimShady\Desktop\Important.txtAs appears above, I found a file named “Important.txt”, which looks very promising. I tried to dump that file using the following command.
CommandLine
$ ./vol -f /home/oviche/Desktop/memlabs/MemoryDump_Lab4.raw --profile=Win7SP1x64 --profile=Win7SP1x64 dumpfiles -Q 0x000000003fc398d0 -D DumpedFiles4
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x3fc398d0 None \Device\HarddiskVolume2\Users\SlimShady\Desktop\Important.txtNo file has been dumped after the previous command. That suggests that the file is no longer in memory. That means that the file is no longer in memory.
So, I directed my thoughts toward Master File Table (MFT), which is a database that holds information for every file and folder in the file system. Also, MFT holds information about deleted files, as long as it’s not overwritten by other files on disk. The information about the deleted files include data content of them if it’s around 600 bytes.
I used the mftparser plugin to extract the MFT records as appear in the following command.
CommandLine
$ ./vol -f MemoryDump_Lab4.raw --profile=Win7SP1x64 mftparser > DumpedFiles4/mft.txtNow, let’s search the “mft.txt” for the “Important.txt” file record. The content of this file appears in the MFT record, as shown below.
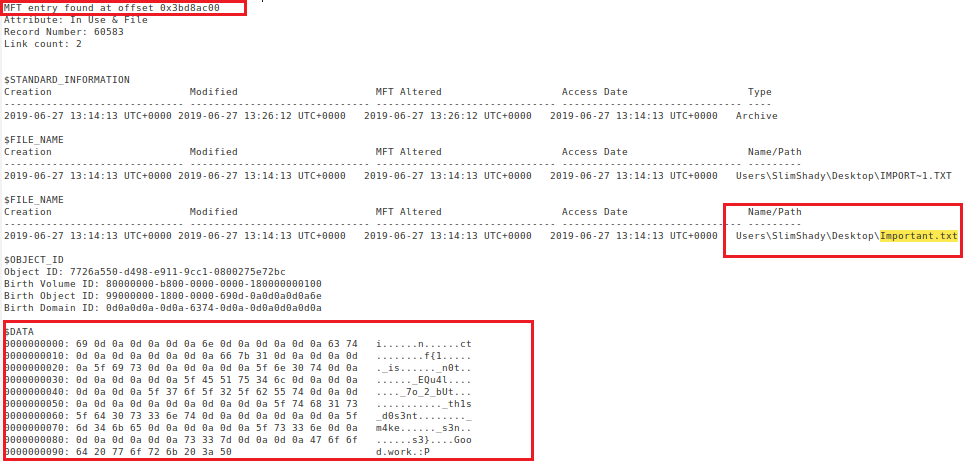 (The MFT record for important.txt)
(The MFT record for important.txt)
To dump the content of the “important.txt”, I used the following command specifying the offset of the file as appears in the following command.
CommandLine
{:.filename}
$ ./vol -f /home/oviche/Desktop/memlabs/MemoryDump_Lab4.raw --profile=Win7SP1x64 mftparser -o 0x3bd8ac00 -D DumpedFiles4By printing the content of the dumped file, the flag characters appear separated by newlines.
CommandLine
$ cat important.txt
i
n
ct
f{1
_is
_n0t
_EQu4l
_7o_2_bUt
_th1s_d0s3nt
_m4ke
_s3n
s3}
Good work :PConclusion
The final solution is the concatenation of the above characters of the flag as below.
inctf{1_is_n0t_EQu4l_7o_2_bUt_th1s_d0s3nt_m4ke_s3ns3}