Introduction
Last time, I posted a solution that shows how I approached the second lab of MemLabs challenges. This post continues to show how I got the flags for the third lab of MemLabs, called “The Evil’s Den”.
Extracting the clues from description
The following is the challenge description that contains the needed clues to solve this lab.
A malicious script encrypted a very secret piece of information I had on my system. Can you recover the information for me please?
Note-1: This challenge is composed of only 1 flag. The flag split into 2 parts.
Note-2: You’ll need the first half of the flag to get the second.
You will need steghide to solve the challenge.
I managed to extract the following two clues:
- A malicious script encrypted a very secret piece of information I had on my system, is a hint to look for a script and understand it.
- You will need steghide to solve the challenge, is a hint that there is data hidden in either image or audio file.
Finding the image profile
First of all, we need to find the profile of the memory image using imageinfo plugin as in the following command.
CommandLine
$ ./vol -f MemoryDump_Lab3.raw imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : FileAddressSpace (/home/oviche/Desktop/memlabs/MemoryDump_Lab3.raw)
PAE type : PAE
DTB : 0x185000L
KDBG : 0x82742c68L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0x82743d00L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2018-09-30 09:47:54 UTC+0000
Image local date and time : 2018-09-30 15:17:54 +0530The first suggested profile “Win7SP1x86_23418” worked in my case.
Locating the malicious script
First, I looked at the running processes using pslist. I discovered two instances of the notepad, which are running as shown below.
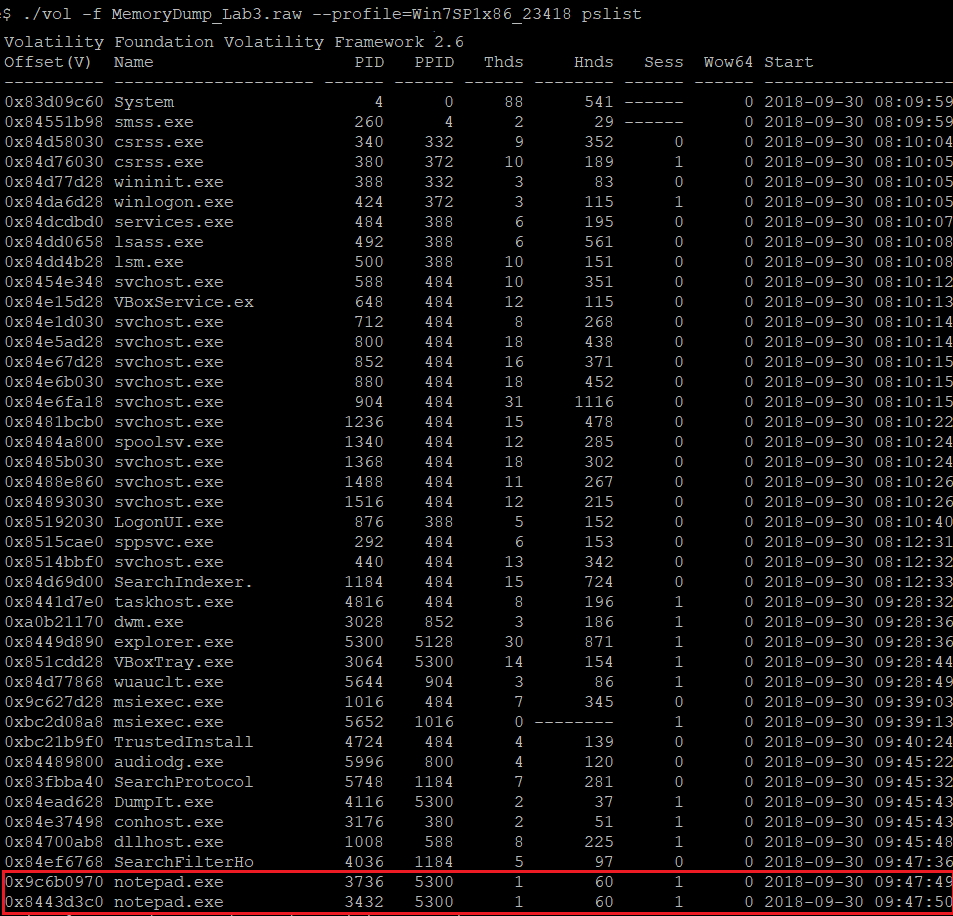 (The running processes)
(The running processes)
So let’s look over the command-line arguments of notepad processes using cmdline plugin.
CommandLine
$ ./vol -f MemoryDump_Lab3.raw cmdline | grep -i "notepad"
Volatility Foundation Volatility Framework 2.6
notepad.exe pid: 3736
Command line : "C:\Windows\system32\NOTEPAD.EXE" C:\Users\hello\Desktop\evilscript.py
notepad.exe pid: 3432
Command line : "C:\Windows\system32\NOTEPAD.EXE" C:\Users\hello\Desktop\vip.txtIn the above result from the cmdline command, the notepad instances open a Python script named evilscript.py and text file vip.txt.
Now we have found the malicious script, let’s dump it to inspect the code.
CommandLine
$ ./vol -f MemoryDump_Lab3.raw --profile=Win7SP1x86_23418 filescan | grep -i "evilscript.py"
Volatility Foundation Volatility Framework 2.6
0x000000003de1b5f0 8 0 R--rw- \Device\HarddiskVolume2\Users\hello\Desktop\evilscript.py.py
$ ./vol -f MemoryDump_Lab3.raw --profile=Win7SP1x86_23418 dumpfiles -Q 0x000000003de1b5f0 -D DumpedFiles
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x3de1b5f0 None \Device\HarddiskVolume2\Users\hello\Desktop\evilscript.py.pyevilscript.py
import sys
import string
def xor(s):
a = ''.join(chr(ord(i)^3) for i in s)
return a
def encoder(x):
return x.encode("base64")
if __name__ == "__main__":
f = open("C:\\Users\\hello\\Desktop\\vip.txt", "w")
arr = sys.argv[1]
arr = encoder(xor(arr))
f.write(arr)
f.close()The script receives a one-string argument as input and then xor its characters with value 0x3. Then, apply base64 encoding on the result and save it to the text file “vip.txt”.
Now let’s dump vip.txt and print its content.
CommandLine
$ ./vol -f MemoryDump_Lab3.raw --profile=Win7SP1x86_23418 filescan | grep -i "vip.txt"
Volatility Foundation Volatility Framework 2.6
0x000000003e727e50 8 0 -W-rw- \Device\HarddiskVolume2\Users\hello\Desktop\vip.txt
$ ./vol -f MemoryDump_Lab3.raw --profile=Win7SP1x86_23418 dumpfiles -Q 0x000000003e727e50 -D DumpedFiles
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x3e727e50 None \Device\HarddiskVolume2\Users\hello\Desktop\vip.txt
$ cat vip.txt
am1gd2V4M20wXGs3b2U=I wrote the following script to decode the text in the vip.txt file.
DecodingVIP.py
import base64
vipText = "am1gd2V4M20wXGs3b2U="
decoded_bytes = base64.b64decode(vipText)
original_str = ''.join(chr(ord(i)^3) for i in decoded_bytes.decode("utf-8"))
print(original_str) # print inctf{0n3_h4lfThis script prints the half flag, which is “inctf{0n3_h4lf”.
Recovering the hidden data
The second hint is that we need to use the steghide tool, which is used to hide data inside images or audio files. Based on the documentation, steghide has support for JPEG, BMP, WAV, and AU files.
Thus, I used these extensions to locate the file that conceal the data. I get lucky using JPEG extension, as appears in the following command.
CommandLine
$ ./vol -f MemoryDump_Lab3.raw --profile=Win7SP1x86_23418 filescan | grep -i "jpeg"
Volatility Foundation Volatility Framework 2.6
0x0000000004f34148 2 0 RW---- \Device\HarddiskVolume2\Users\hello\Desktop\suspision1.jpegI dumped a JPEG image named “suspision1.jpeg”.
CommandLine
$ ./vol -f MemoryDump_Lab3.raw --profile=Win7SP1x86_23418 dumpfiles -Q 0x0000000004f34148 -D DumpedFiles
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x04f34148 None \Device\HarddiskVolume2\Users\hello\Desktop\suspision1.jpeg (suspision1.jpeg)
(suspision1.jpeg)
I used the following command with password “inctf{0n3_h4lf” (as the second part of the flag depends on the first part) to extract the hidden data from the image.
CommandLine
$ steghide extract -sf suspision1.jpeg
Enter passphrase:
wrote extracted data to "secret text".The hidden data is written to the “secret text” file. So, let’s print the content of that file.
CommandLine
$ cat 'secret text'
_1s_n0t_3n0ugh}The second half of the flag is “_1s_n0t_3n0ugh}”
Conclusion
The final solution is the concatenation of the half flags as below.
inctf{0n3_h4lf_1s_n0t_3n0ugh}