Introduction
I decided to refresh my memory forensics knowledge by going through MemLabs CTF-styled challenges and this post is writeup for the first challenge named “Beginner’s Luck”.
Extracting the clues from the description
The following is the statement of the challenge that contains the clues that should be extracted to plan how to approach the challenge.
My sister’s computer crashed. We were very fortunate to recover this memory dump. Your job is get all her important files from the system. From what we remember, we suddenly saw a black window pop up with some thing being executed. When the crash happened, she was trying to draw something. Thats all we remember from the time of crash.
The following three important clues are noticed:
- “Your job is get all her important files from the system”; so first mission is recover her important files.
- “we suddenly saw a black window pop up with some thing being executed”; Thus, the second mission is to check the CMD’s executed commands.
- “When the crash happened, she was trying to draw something”; Hence, the third mission is to find what she was drawing at the time.
Recovering the important files
Before starting to look for the important file, the profile of the memory image must be identified using the following command of volatility and the first profile (Win7SP1x64) worked for me.
CommandLine
$ ./vol -f MemoryDump_Lab1.raw imageinfo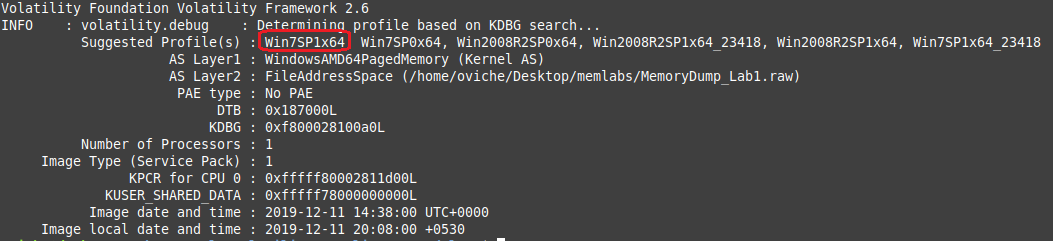 (The suggested profiles)
(The suggested profiles)
Now, we can start looking for the important files using the filescan plugin as shown below.
CommandLine
$ ./vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 filescan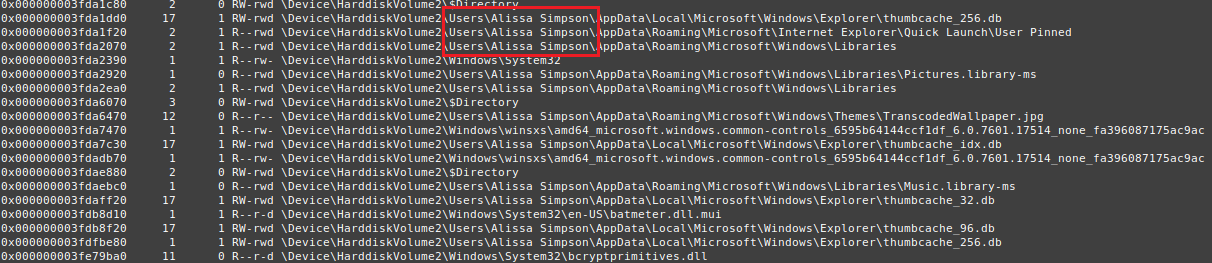 (The results from filescan plugin)
(The results from filescan plugin)
As appears in the above screenshot, a lot of file objects were found. However, we can narrow the search results down to the files from the “Alissa Simpson” directory as we search for the files for a girl based on the challenge description.
So the following command is used to find the search results for the “Alissa Simpson” directory.
CommandLine
$ ./vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 filescan | grep "Alissa Simpson"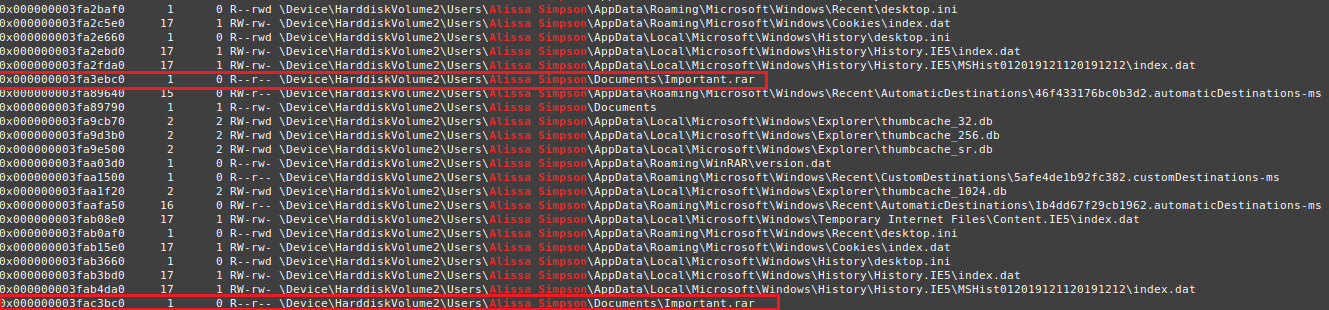 (Files from Alissa Simpson directory)
(Files from Alissa Simpson directory)
As noticed in the above screenshot, there are files named important.rar and based on the challenge statement, we need to find her “important” files. Thus, let’s dump the file from memory using the following command.
CommandLine
$ ./vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003fac3bc0 --name importantFile.rar -D DumpedFiles/
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x3fac3bc0 None \Device\HarddiskVolume2\Users\Alissa Simpson\Documents\Important.rarAs appears in the below screenshot, when I tried to decompress the file, I found that it’s protected with a password which is uppercase of NTLM hash for the Alissa password.
CommandLine
$ unrar x importantFile.rar
UNRAR 6.11 beta 1 freeware Copyright (c) 1993-2022 Alexander Roshal
Extracting from importantFile.rar
Password is NTLM hash(in uppercase) of Alissa's account passwd.
Enter password (will not be echoed) for flag3.png:Now let’s use a volatility plugin called hashdump to extract NTLM for Alissa Simpson that equals f4ff64c8baac57d22f22edc681055ba6. Then we convert its characters to uppercase to get the password for rar file.
CommandLine
$ ./vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 hashdump | grep "Alissa"
Volatility Foundation Volatility Framework 2.6
Alissa Simpson:1003:aad3b435b51404eeaad3b435b51404ee:f4ff64c8baac57d22f22edc681055ba6:::After successfully decompressing the rar file, the following image is found which contains the third flag.
 (The image file containing the third flag)
(The image file containing the third flag)
Discovering CMD’s executed commands
Now, we move to the second clue which states that a black window (probably CMD) with something being executed (referring to command execution). To confirm this thought, we need to check the running processes list using the pslist plugin.
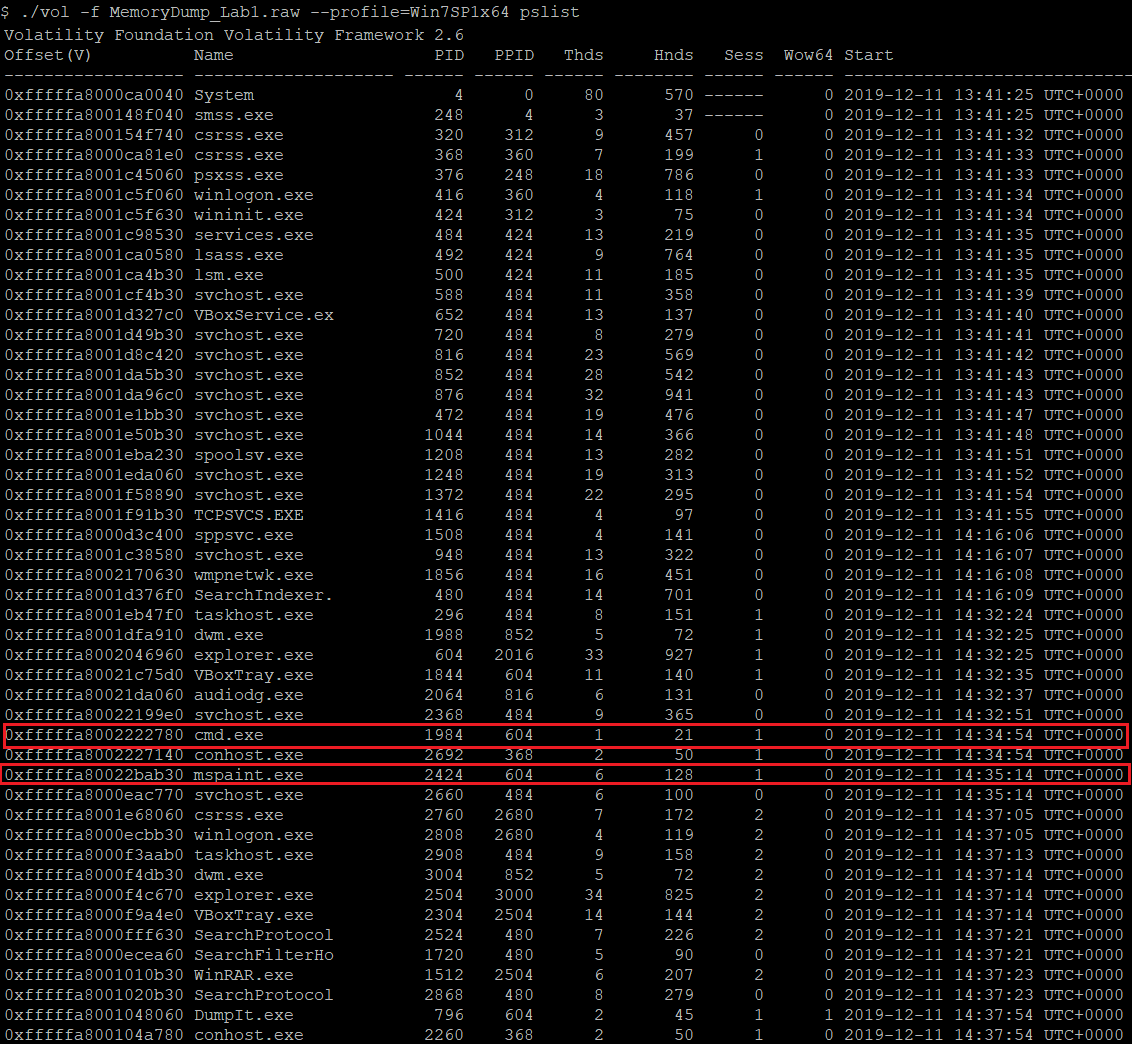 (The list of running processes)
(The list of running processes)
As appears in the above screenshot, there are two interesting processes which are cmd.exe and mspaint.exe. However, let’s focus on the cmd.exe process as it’s related to the current clue.
In order to extract the executed commands and their output, the plugin consoles is used as appears below.
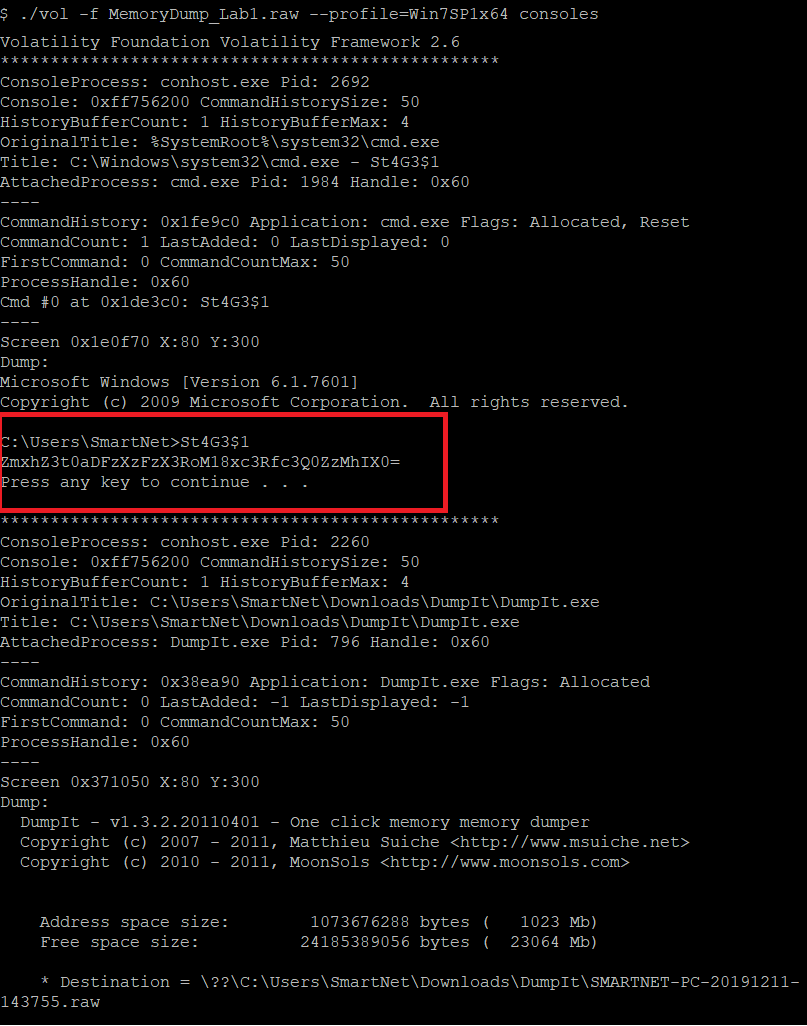 (The executed commands)
(The executed commands)
The above screenshot shows that when the highlighted command gets executed, a base64 encoded string “ZmxhZ3t0aDFzXzFzX3RoM18xc3Rfc3Q0ZzMhIX0=” is printed.
By decoding it we get the first flag flag{th1s_1s_th3_1st_st4g3!!}.
Recovering the picture she was drawing
Finally, we need to recover the image that she was drawing at the time of the crash. Based on the processes list, the only executable that can be used to draw is mspaint.exe. Therefore, the image exists in this process memory.
First, The process memory of the mspaint.exe is dumped using the memdump plugin as in the following command.
CommandLine
$ ./vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 memdump -p 2424 -D DumpedFiles
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing mspaint.exe [ 2424] to 2424.dmpAfter that, The gimp program will be used to try to recover the image from the dumped memory. The memory dump must be renamed from 2424.dmp to 2424.data to be opened by gimp. By playing around with offset and width sliders, I successfully found the picture but it’s mirrored.
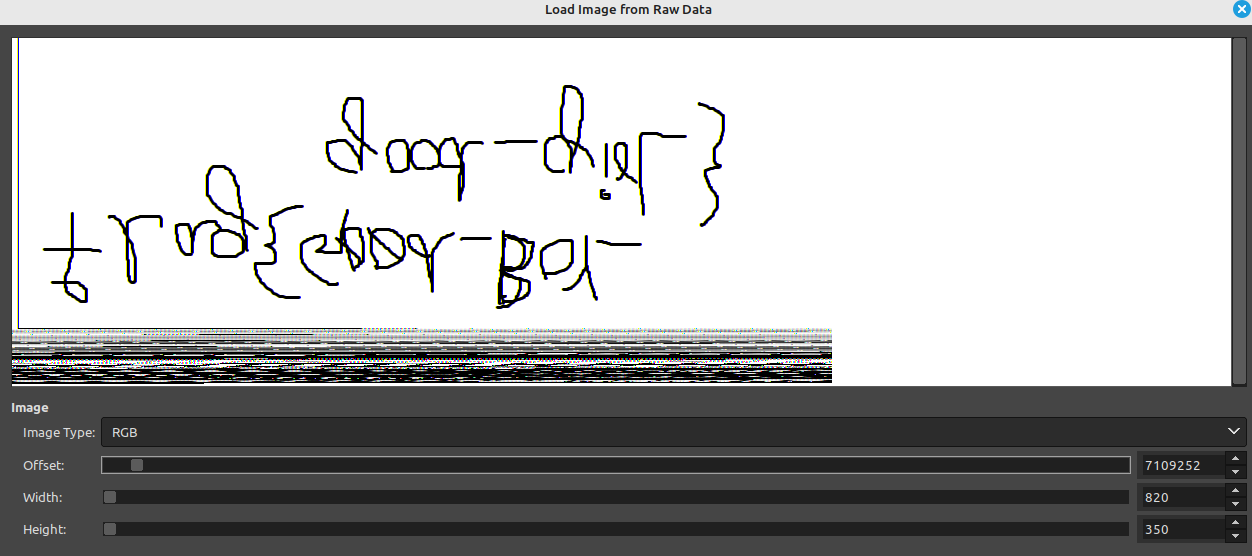 (Recovered drawing from ms-paint)
(Recovered drawing from ms-paint)
Finally, by performing a flip horizontally and rotating 180, the flag becomes readable as appears below.
 (The Second flag)
(The Second flag)
Conclusion
The final solution is the concatenation of flags as below.
flag{th1s_1s_th3_1st_st4g3!!} flag{G00d_BoY_good_girL} flag{w3ll_3rd_stage_was_easy}